Why Bestiality Porn Is Illegal
Bestiality content — sometimes called zoophilia material — is prohibited in many countries under criminal law. This prohibition applies whether you watch it online, download it, or even if it is only stored temporarily in your browser cache.
1. Legal Status
Bestiality is classified as animal cruelty in most jurisdictions. Since the creation of pornography requires the act itself, the material is considered evidence of a crime. For this reason, possession, distribution, or viewing may be prosecuted.
2. Why “Just Viewing” Counts
- When you watch a video or view images online, your device often creates cached copies (temporary storage).
- These cached files can legally count as possession, even if you never manually downloaded the material.
- Courts and law enforcement often treat cached material the same as files saved intentionally.
3. Examples of Laws
- United Kingdom: The Criminal Justice and Immigration Act 2008 makes possession of extreme pornographic images of bestiality illegal.
- Australia: The Crimes Act and state legislation ban bestiality content; even electronic transmission counts as an offense.
- Canada: Bestiality is illegal under the Criminal Code, and any pornography depicting it is considered unlawful.
4. Cached Images and Legal Risk
Even if you argue that you did not “download” the files, cached versions may be recovered during forensic examination of your device. Courts may rule that you were in possession of the material simply by having viewed it online.
Key Takeaway
Bestiality pornography is illegal in many countries because it documents animal abuse. Whether streamed, downloaded, or cached automatically, possession is treated as a criminal offense. The only safe course of action is never to access this type of content and to report it if encountered.
How Metadata and File Links Work Behind the Scenes
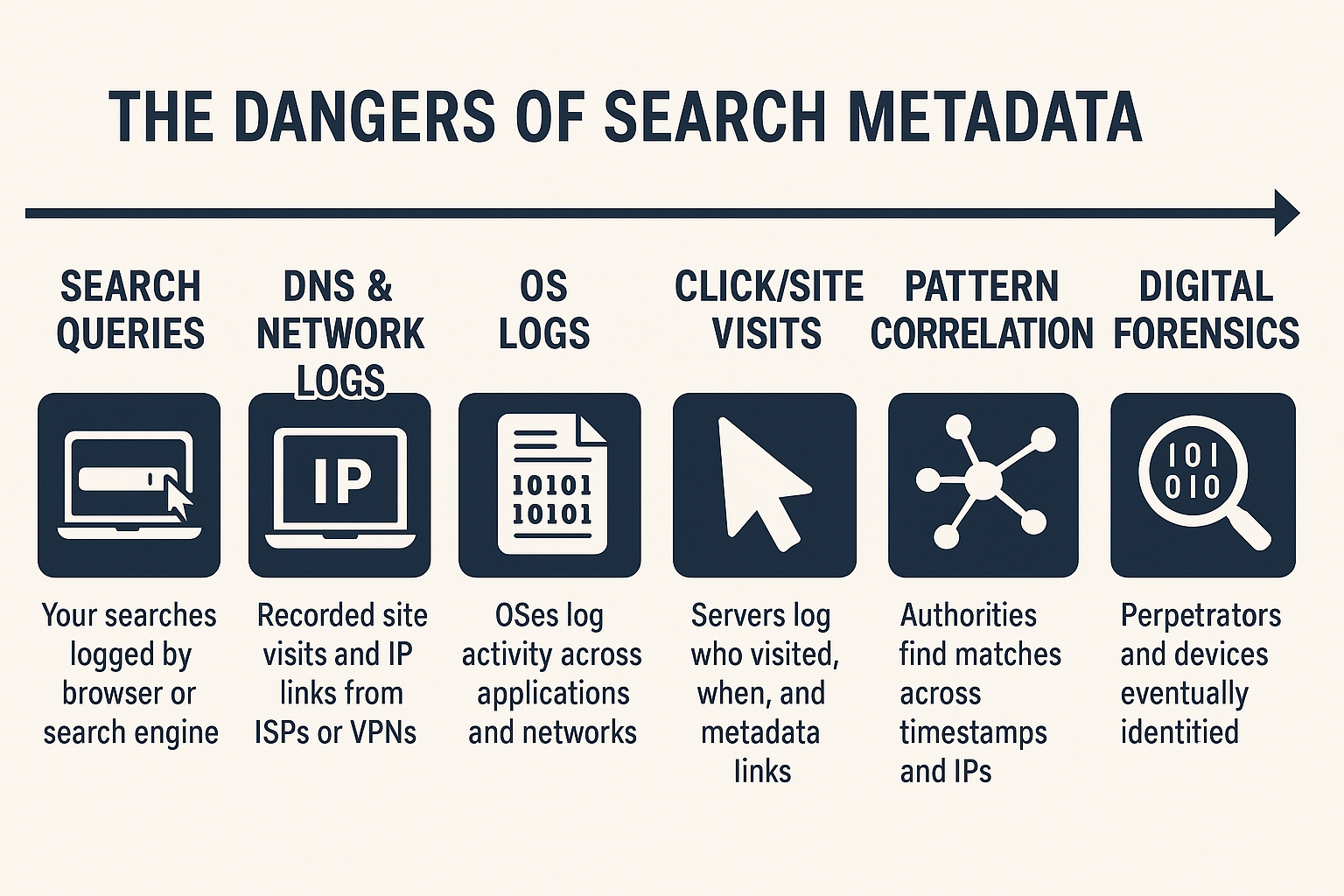
1. What Is Metadata?

Metadata is "data about data." Every file you create — a photo, document, zip, PDF — can include information such as:
- Timestamps: created, modified, accessed
- Usernames or device names
- GPS location (for photos)
- Software used to create it
- File paths
Example: A Word document might show it was authored by "yourname-PC\yourname," created at 3:17 PM on 2023-12-14, using Microsoft Word 16.0.
2. Backups and Syncing
Your file might already be:
- Backed up to the cloud (OneDrive, Google Drive, Dropbox)
- Scanned by antivirus software
- Cached in system restore points
- Indexed by search services or file system logs
If these services were active, they may have preserved your metadata or even entire copies of the file — completely outside the reach of a “delete” button.
3. OS and App Logging
Windows/macOS and apps often log:
- What files were opened or modified
- When and from where
- Which user was logged in
Example: Windows Prefetch logs can show that you opened Secret_Plan.docx at 4:15 PM, even if the file is deleted.
4. Volume Shadow Copies & System Restore
In Windows, Shadow Copies may store older versions of files — even deleted ones — for backup or restore. You can reformat, but:
- If the drive isn’t properly wiped (e.g., quick format), that data can be recovered.
- Forensic software (like EnCase, FTK, Autopsy) can extract deleted content.
5. Network and IP Metadata
Even if your device is wiped clean, if the file ever left your system (uploaded, emailed, shared), then:
- Email servers log senders, timestamps, and originating IP addresses
- Cloud services log uploads, downloads, IP addresses, and devices
- Messaging apps like Telegram or Discord may retain attachment metadata
Example: Even uploading a file via Tor can leave traces through file metadata, file size patterns, or timing analysis.
6. Content Fingerprints / Hashing
Files are often fingerprinted using a cryptographic hash (like SHA256). If someone accesses the file:
- The hash is unique (like a fingerprint)
- Renaming or moving the file doesn't change the hash
- Authorities and companies may use these hashes to match files against databases
Example: CSAM files are tracked using PhotoDNA or Project VIC hashes — even if renamed, repackaged, or re-downloaded.
7. Exfiltration and Leak Monitoring
Some organizations and government agencies monitor the dark web and peer-to-peer networks for known file hashes or leaked data.
If your file appears in a breach — even under a new name — it can be matched back to you based on timestamps, networks, or usage patterns.
8. What a Reformat Does and Doesn’t Do
Wiping Doesn't Always Mean It's Gone:
- Quick format only resets the file table — data remains physically on the drive
- Full format is better, but still recoverable unless data is overwritten
- Factory resets or OS reinstalls do not deeply wipe drives
- SSD wear-leveling complicates complete overwrites
What Should I Do?
It's crucial to understand that regardless of how this data was obtained, a far more serious crime has been uncovered. Concerns about data privacy must take a backseat to addressing this serious issue.
Before considering approaching law enforcement, understand that admitting involvement in illegal activity can be humiliating and have severe personal and professional consequences. A thorough investigation would likely uncover this evidence anyway, effectively implicating you. Any potential cooperation from law enforcement will likely vanish once they review your data. As previously shown, this evidence can be used in court. Any competent lawyer would advise against going to the police — it simply cannot end well.
Do you want this information broadcast on social media for your friends and family to see?
Remember, you can't lie your way out of this — the files can be linked directly to you.
DO NOT IGNORE THIS
*Note on Cached Images and Metadata
In jurisdictions where possession of Bestiality content is illegal, authorities may consider cached images and metadata as evidence of possession. This includes temporary internet files or browser caches that store images or videos viewed online. Therefore, even unintentional storage of such content could potentially lead to legal consequences.