How You Can Be Tracked
If your data is in someone's possession, you should not ignore it
CSAM (child sexual abuse material) is strictly illegal worldwide, and law enforcement actively tracks it. This includes images, cartoons, AI-generated material, and in some jurisdictions, even written stories.
Example: In Australia, written text depicting child abuse is considered illegal. In the United States, United States v. Steiger (2003) showed how data obtained by private citizens could be admitted in court. In the UK, evidence law permits the use of unlawfully obtained data in criminal proceedings.
Many countries allow such evidence when investigating CSAM due to the severity of the crime.
How Metadata and File Links Work Behind the Scenes
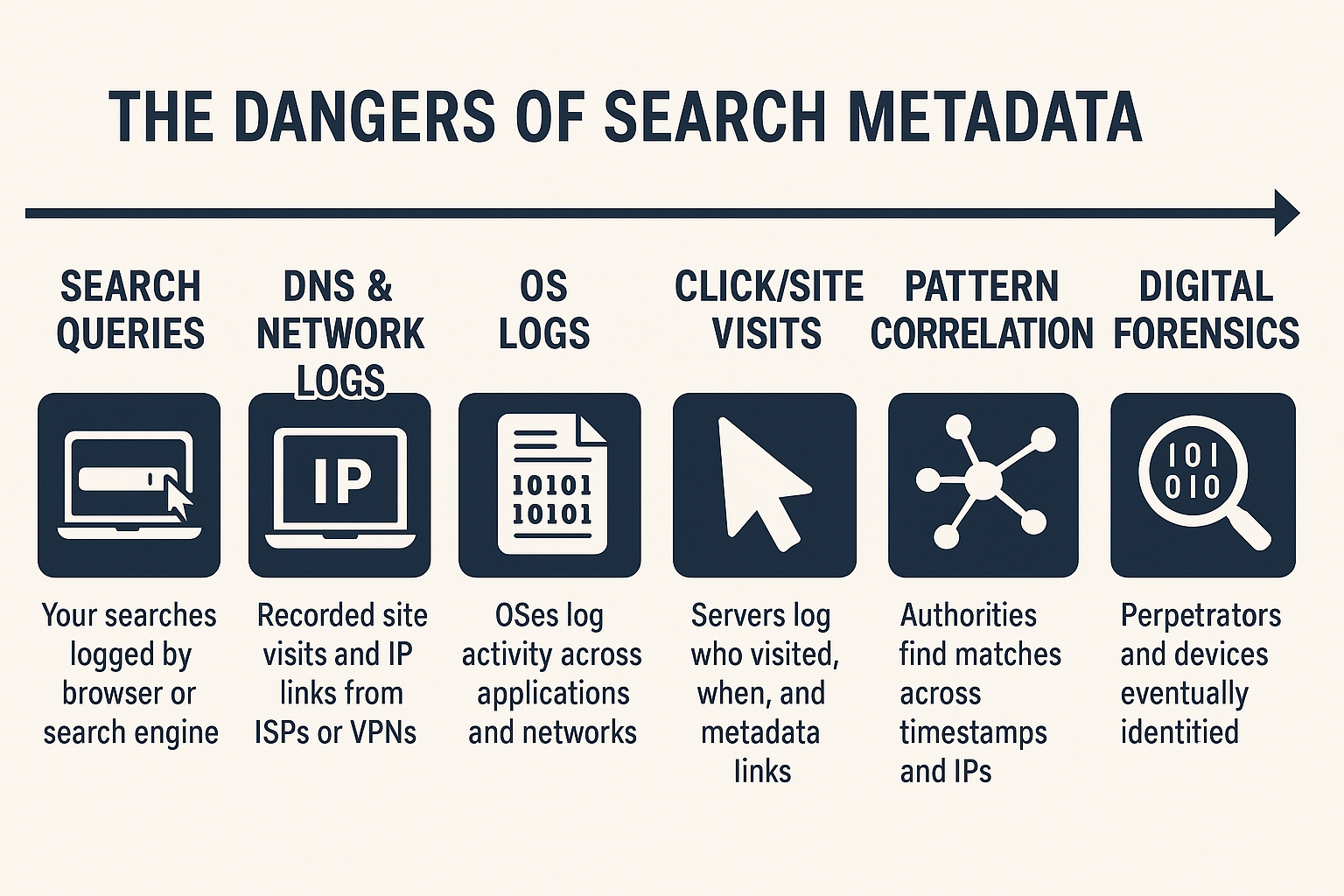
1. What Is Metadata?
Metadata is "data about data." Every file — photo, document, PDF — may include:
- Timestamps (created, modified, accessed)
- Usernames or device names
- GPS location (for photos)
- Software used to create it
- File paths
2. Backups and Syncing
Your file might already be saved elsewhere without you realizing:
- Cloud backups (OneDrive, Google Drive, Dropbox)
- Antivirus scans
- System restore points
- Search indexes or file logs
3. OS and App Logging
Operating systems and apps can log what files were opened, when, and by which user. For example, Windows Prefetch may show if you opened a deleted file.
4. Volume Shadow Copies & System Restore
Even deleted files may exist in shadow copies or restore points. Forensic tools can recover this data unless the drive is properly wiped.
5. Network and IP Metadata
Once shared online, files leave traces:
- Email headers show sender and IP
- Cloud logs track uploads and downloads
- Messaging apps may keep attachment metadata
6. Content Fingerprints / Hashing
Files can be tracked using unique hashes (like SHA256). Renaming a file won’t change its fingerprint. Authorities and companies maintain hash databases (PhotoDNA, Project VIC).
7. Exfiltration and Leak Monitoring
Law enforcement and researchers monitor networks for known file hashes. If your file surfaces again, it can be traced back to you.
8. What a Reformat Does and Doesn’t Do
Reformatting doesn’t always erase data:
- Quick format leaves data on disk
- Full format is better but may still be recoverable
- Factory resets don’t deeply wipe drives
- SSDs complicate overwriting due to wear-leveling
9. The Myth of Tor Anonymity
Using Tor may hide your IP address, but it does not make you invisible. Many people are identified not through their connection, but through their behavior.
- If you reuse the same usernames or passwords on Tor sites that you also use on legal websites, investigators can connect those identities.
- Even variations of usernames (adding numbers or small changes) can often be linked back to your real accounts.
- Email addresses, recovery questions, and password patterns are strong identifiers.
- Once an account is connected to you, Tor provides no protection against attribution.
Authorities routinely monitor hidden services. Accounts created with reused or similar credentials are one of the easiest ways people are unmasked, regardless of Tor or VPN use.
Key Takeaway
Whether intentional or not, possession of illegal content can be proven through metadata, logs, and forensic recovery. Deleting files does not guarantee safety. Cached images or temporary files may also count as possession under the law.
Do not ignore this. If you encounter illegal material, the only safe and legal action is to report it immediately.
What Should I Do?
It's crucial to understand that regardless of how this data was obtained, a far more serious crime has been uncovered. Concerns about data privacy must take a backseat to addressing this serious issue.
Before considering approaching law enforcement, understand that admitting involvement in illegal activity can be humiliating and have severe personal and professional consequences. A thorough investigation would likely uncover this evidence anyway, effectively implicating you. Any potential cooperation from law enforcement will likely vanish once they review your data. As previously shown, this evidence can be used in court. Any competent lawyer would advise against going to the police — it simply cannot end well.
Do you want this information broadcast on social media for your friends and family to see?Remember, you can't lie your way out of this — the files can be linked directly to you.
Finally, we would like to point out that YOU are the one who can be fully identified in this matter and you wouldn't be in this situation had you not been searching this content.
DO NOT IGNORE THIS
*Note on Cached Images and Metadata
In jurisdictions where possession of Rape Pornography content is illegal, authorities may consider cached images and metadata as evidence of possession. This includes temporary internet files or browser caches that store images or videos viewed online. Therefore, even unintentional storage of such content could potentially lead to legal consequences.